hash256|SHA256 Hash Generator Online Tool : Tagatay SHA512 hash function generator generates a SHA512 hash which can be used as . The second largest city in the Netherlands, Rotterdam is home to one of the biggest and busiest port on earth, with numerous waterways and canals crisscrossing the city. Having sustained considerable damage during the Second World War, the city is now characterized by futuristic and innovative architecture, although there is still an .
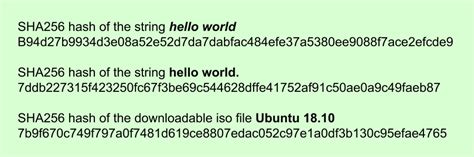
hash256,SHA256 hash function generator generates a SHA256 hash (SHA256 Encode) which can be used as secure 64 char password or used as Key to protect important data such as personal .SHA384 hash function generator generates a SHA384 hash which can be used as .SHA512 hash function generator generates a SHA512 hash which can be used as .
This online SHA256 Hash Generator tool helps you to encrypt one input string into a fixed 256 bits SHA256 String. Paste your Input String or drag text file in the first textbox, then press .SHA-256 is a hash standard that converts any binary data to a 64-character fingerprint. Learn how to encrypt and decrypt a character string or a file using SHA-256, and see examples and .
Learn what SHA-256 Hash is, how it works, and why it's important for cryptography. Explore the history, security, and applications of this hash function .Secure Hash Algorithm 256 (SHA-256) is a widely used cryptographic hash function that generates a fixed-size output (256 bits) from any given input. The output is typically .

Generate a SHA-256 hash with this free online encryption tool. To create a SHA-256 checksum of your file, use the upload feature. To further enhance the security of you encrypted hash you .
SHA256 Hash Generator Online Tool SHA-256 is a popular cryptographic hash function that generates a 256-bit signature from any input text. Learn how it works step by step, what it is used for, and why it is secure and fast.
When passwords are stored, they are usually salted to prevent an attacker from cracking the passwords of many users who happen to have chosen the same password, at once. Finally, .
Learn what SHA-256 is, how it works, and why it's important for data security. This comprehensive guide covers the basics, the process, the applications, and the limitations of . Learn what hashing is, how SHA-256 works, and what its features and applications are. SHA-256 is a popular and widely used algorithm for data security, digital .备案号:闽ICP备16008567号-1 [email protected] QQ:1878399009 md5互助群:303488034 友情链接: 上班摸鱼神器-单行阅读器 奇乐浓浓小说网 SecSilo Mrxn's Blog 七行者博客 Arvin's Blog 本站所有用途仅限于使用在法律允许的范围下,如果发现有违法行为,将立即封停账号!闽ICP备16008567号-1hash256 SHA256 Hash Generator Online Tool 这个sha256加密在线工具可以帮助您将一个输入字符串加密为固定的256位sha256字符串.Hash256() returns a 256-bit hash of the combined input expression values. The result is a 43-character string. The result is a 43-character string. Syntax:
像sha-256和sha2这样的密码散列函数在保护数据方面发挥着重要作用,应用范围从软件更新到加密货币。在本文中,我们将揭秘这些算法是什么,它们是如何工作的,以及为什么sha-256在验证完整性方面如此普遍。 Java applications have a notoriously slow startup and a long warmup time. The CRaC (Coordinated Restore at Checkpoint) project from OpenJDK can help improve these issues by creating a checkpoint with an application's peak performance and restoring an instance of the JVM to that point.. To take full advantage of this feature, BellSoft provides containers that are .
SHA-2 (Secure Hash Algorithm 2), of which SHA-256 is a part, is one of the most popular hash algorithms around. A cryptographic hash, also often referred to as a “digest”, “fingerprint” or “signature”, is an almost perfectly unique string of characters that is generated from a separate piece of input text. SHA-256 generates a 256-bit (32-byte) signature.
sha256ハッシュの生成ツールです。 最終更新: 2015/06/30 , 公開: 2015/06/30学习区块链,总是无法避开各种加密算法,因为各种加密算法在实现区块链当中的各个环节都有着不可替代的作用。这里介绍一下在比特币挖矿以及merkle树当中被大量使用的鼎鼎大名的SHA256算法。 SHA-2 族算法简介一个 .
hash256学习区块链,总是无法避开各种加密算法,因为各种加密算法在实现区块链当中的各个环节都有着不可替代的作用。这里介绍一下在比特币挖矿以及merkle树当中被大量使用的鼎鼎大名的SHA256算法。 SHA-2 族算法简介一个 . Stack Overflow for Teams Where developers & technologists share private knowledge with coworkers; Advertising & Talent Reach devs & technologists worldwide about your product, service or employer brand; OverflowAI GenAI features for Teams; OverflowAPI Train & fine-tune LLMs; Labs The future of collective knowledge sharing; About the company .
Calcula un hash SHA con 256 bits. Genera un hash SHA-256 con esta herramienta online y gratuita de cifrado. Para crear una suma de chequeo SHA-256 de tu archivo, usa la función de subir un fichero.SHA(Secure Hash Algorithm)是一组密码学哈希函数,用于将任意长度的数据转换成固定长度的哈希值。SHA算法广泛用于数据完整性验证、数字签名、密码学安全等领域。SHA家族包括多个版本,其中较常见的有SHA-1、SHA-256、SHA-384和SHA-512等。 安全散列算法(英语:Secure Hash Algorithm,缩写为SHA)是一个密码 .
Dive into our SHA-256 tutorial and learn the ins and outs of this secure hash algorithm, from its workings to practical applications and more!
This project provides a concise and well-documented implementation of the SHA-256 cryptographic hash function in C++. It's designed for easy integration into C++ projects, making it a valuable resource for data integrity verification, password hashing, and digital signatures. - GitHub - kibonga/sha256-cpp: This project provides a concise and well-documented .

sha256 онлайн шифрование. Хеш-функция из семейства алгоритмов sha-2 предназначена для создания «отпечатков» или «дайджестов» для сообщений произвольной длины. Применяется в различных приложениях или компонентах . Hash funciton이라는 게 있습니다. 다양한 길이의 input을 받아서 정해진 길이의 output을 출력하는 함수.SHA256 hash. Herramienta online para la creación de hash SHA256 de una cadena. Generar mensaje SHA256 digerir de una cadena arbitraria usando esta utilidad gratuita de hash SHA256 línea.Hash256 - script and chart function. Hash256() returns a 256-bit hash of the combined input expression values. The result is a 43-character string. Syntax: Hash256(expr{, expression}) Return data type: string. Example: Chart expressions A hash function is referred to as a "cryptographic hash function" if it achieves these 3 strong properties.. This means that it's usually slower than a basic hash function (although still pretty fast overall), but it also means it can be relied upon to be unpredictable and produce unique results for different pieces of data. Which is an important feature when it comes to .
hash256|SHA256 Hash Generator Online Tool
PH0 · What is SHA
PH1 · What Is SHA
PH2 · SHA256 Hash Generator and Calculator Online Tool
PH3 · SHA256 Hash Generator Online Tool
PH4 · SHA256 Generator
PH5 · SHA
PH6 · Generate a SHA
PH7 · Encrypt Online
PH8 · A Definitive Guide to SHA